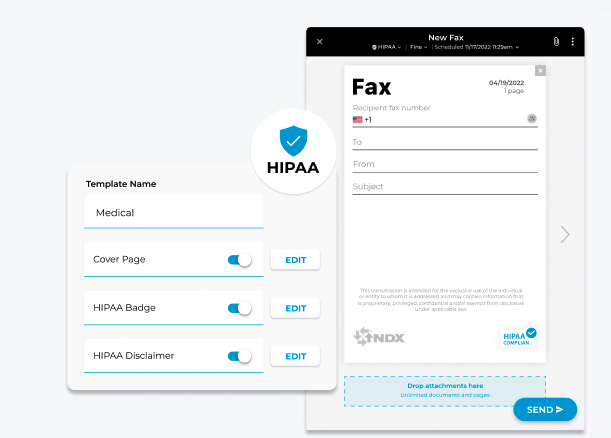
In the event of loss or theft of a device that could potentially access customer data, we follow strict protocols to mitigate any risks:
Incident Reporting: All employees are required to immediately report the loss or theft of any device
Remote Wipe: Upon notification of a device loss or theft, our IT department initiates a remote wipe, if possible, to erase all information and prevent unauthorized access to any sensitive data.
Access Revocation: We also immediately revoke access permissions linked to the lost or stolen device, blocking any potential unauthorized attempts to access our systems or data.
Investigation: We conduct a thorough internal investigation to understand the circumstances of the loss and the potential data exposure.
Notification: In the unlikely event that any customer data is at risk, we follow legal and regulatory requirements to promptly notify the affected customers and guide them through any necessary steps.
Prevention Measures: Post-incident, we review and update our security policies and procedures as necessary to prevent similar occurrences in the future.